In today’s world, where everything from coffee machines to industrial equipment is connected to the network, knowing and assessing the security of your software and its dependencies has never been more important. Most vulnerabilities originate from small bugs in software components, and more recently (and thankfully less frequently) from sophisticated supply chain attacks. But with devices exposed to the internet, those bugs can become entry points for attackers on the other side of the world.
Modern systems are also built on a large foundation of open-source components: libraries, kernels, build tools, and third-party dependencies that make up a significant share of the final firmware image. While open source accelerates innovation and helps spread development costs, it also introduces a continuous flow of upstream updates and vulnerability disclosures that teams must track and manage.
SBOMs (Software Bill of Materials) have emerged as a best practice for making this software composition transparent. However, scanning SBOMs for vulnerabilities is often harder than it should be, especially in embedded environments, where many product designers lack cybersecurity expertise and the resources to perform full audits without automated tools.
Furthermore, the EU Cyber Resilience Act (CRA) mandates that manufacturers of connected products with digital elements create and maintain a Software Bill of Materials that documents components and vulnerabilities and serves as the basis for continuous monitoring as new issues emerge. While public disclosure is not required, manufacturers must provide this information to market surveillance authorities upon request.
That’s why we created VulnScout: to help organizations achieve their security and compliance requirements for the embedded systems they develop.
VulnScout is an SBOM-first vulnerability scanner designed to be developer-friendly and easy to integrate with Yocto, Buildroot, and most systems that generate SBOMs. It supports SPDX, CycloneDX, and OpenVEX SBOMs, enabling streamlined vulnerability detection and exploration at the build level with minimal setup and configuration. It bridges the gap between security tooling and day-to-day software development, particularly in projects with dozens or hundreds of open-source dependencies.
Limitations of Current SBOM Scanners
Many existing tools are excellent at what they do, but they often come with trade-offs that limit their usefulness as a single source of truth for project-level vulnerability assessment:
- Grype is powerful and lightweight but lacks fix tracking or SBOM enrichment.
- Dependency-Track provides a full-featured dashboard but requires centralized infrastructure with a server and database setup.
- Anchore’s tools focus on containerized environments and cloud-native workflows.
But what if you just want to:
- Scan SBOM files generated by Yocto, Buildroot, or any existing build system or distribution
- Merge results from SPDX, CycloneDX, or Yocto outputs
- Explore, sort, filter, track, and document what’s fixed vs. what’s still a risk, including which open-source components are still vulnerable
- Do all of this from a web-based interface, without setting up a server
That’s where VulnScout comes in.
What Sets VulnScout Apart
Unlike many other tools that require a persistent web and database infrastructure, VulnScout is fully self-contained. It runs locally, stores its state within your project repository, and integrates directly with your build system, making CVE assessments version-controlled and part of your release process.
VulnScout helps teams keep track of which components are vulnerable, which ones have been fixed, and which ones still need attention. This history is preserved in the repository, making it part of your engineering workflow and auditable over time.
While other solutions are tightly coupled to specific data formats, VulnScout is format-agnostic and supports SPDX 2.x, SPDX 3.0, CycloneDX, and OpenVEX out of the box, eliminating the need for format conversion. VulnScout can also act as a conversion and reporting tool, allowing you to transform SBOM inputs into:
- Structured SBOMs
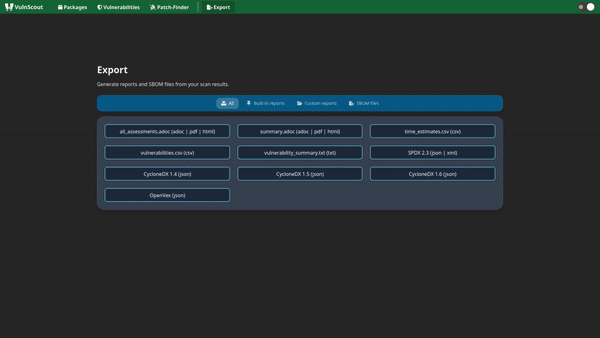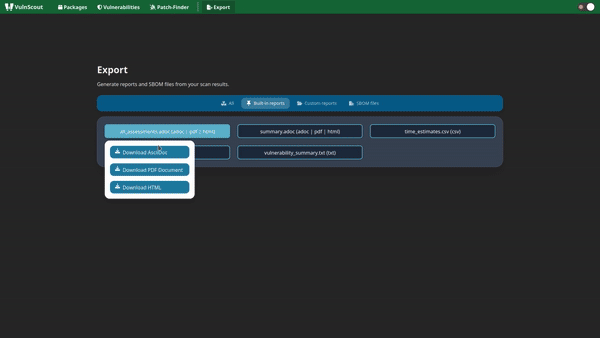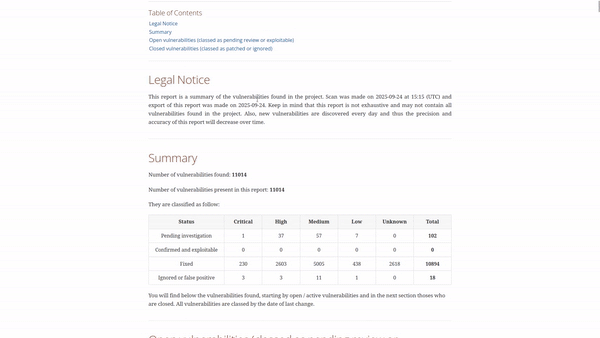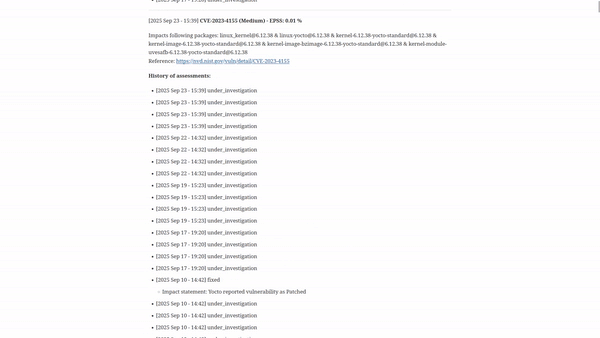
- Human-readable reports (PDF, text, HTML)
- CLI summaries for quick CI/CD integration
This makes it ideal for both automated builds and preparing audit documentation, especially when you need to demonstrate how you’ve addressed vulnerabilities across your open-source dependencies.
How VulnScout Works
Instead of analyzing binaries or source code directly, VulnScout focuses on SBOM inputs. It consumes formats like SPDX, CycloneDX, Grype JSON, and Yocto CVE-check JSON, enriching them with data from:
- NVD (National Vulnerability Database)
- EPSS (Exploit Prediction Scoring System)
- OSV (Open Source Vulnerabilities) (coming soon)
- Grype-compatible data sources
- Vulnerability information already embedded in the SBOM files
 Click to open the video
Click to open the video
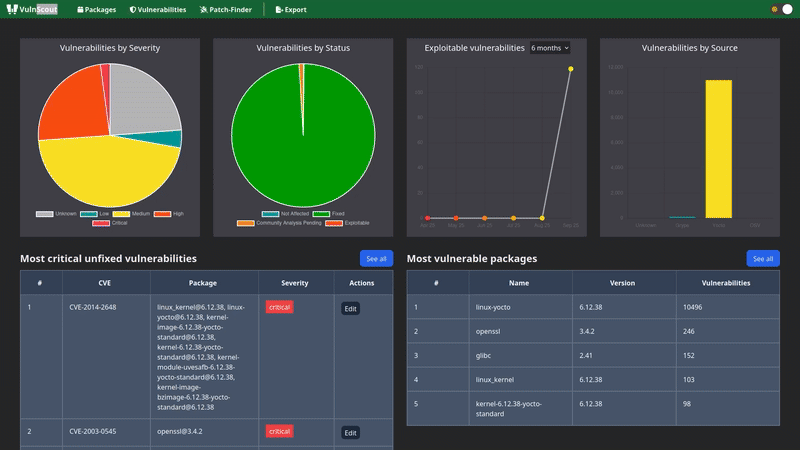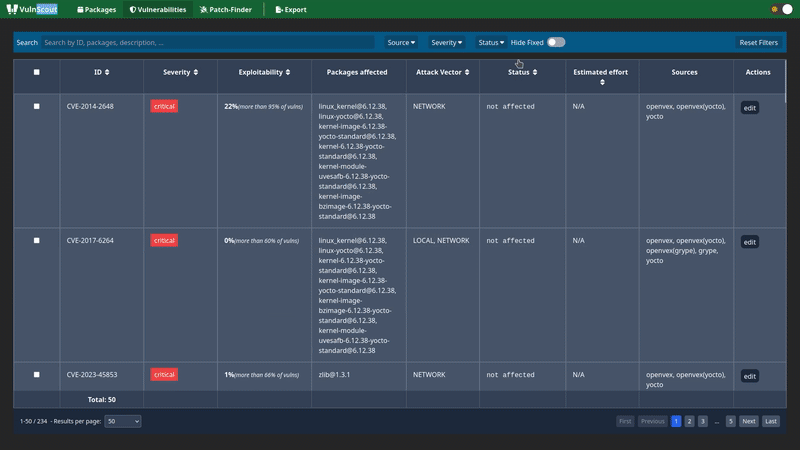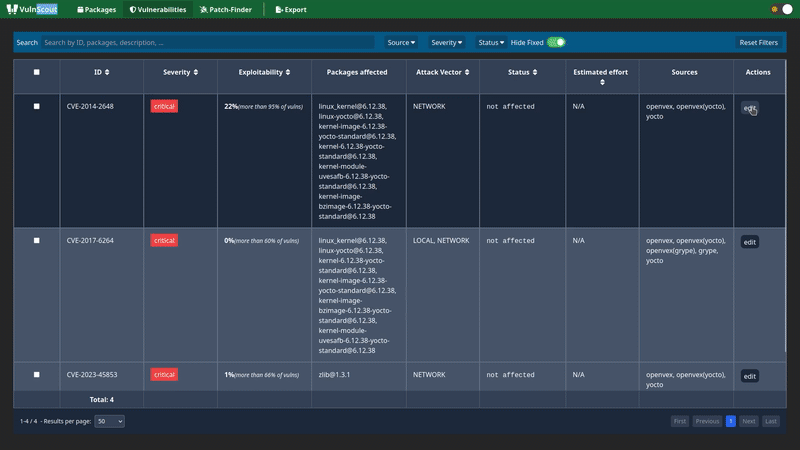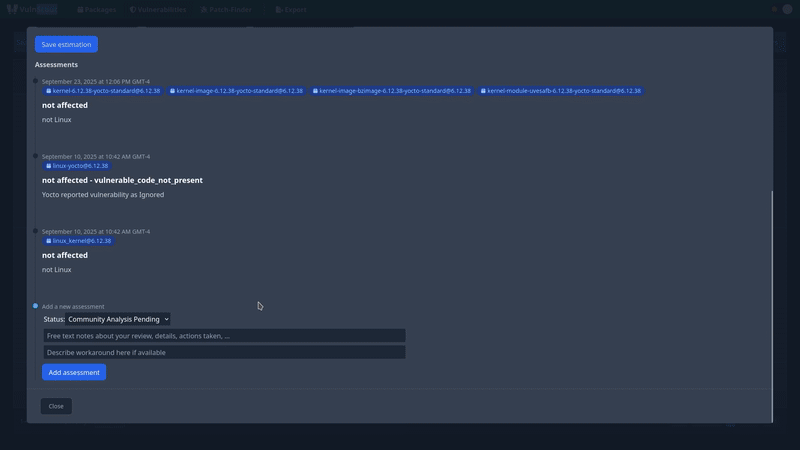
Once scanned, VulnScout generates:
- Rich web-based dashboards
- Extended reporting in PDF, CSV, and text
- Structured output files (SPDX, CycloneDX, OpenVEX)
- CLI summaries for quick integration
- CI alerts based on filters (for example: a new vulnerability with EPSS score > 7.0)
It is designed to run locally, either plugged into a Yocto or Buildroot setup or via a Docker container, and can be triggered with a single script (vulnscout.sh) or a Yocto layer (meta-vulnscout). This workflow allows you to continuously monitor open-source components as part of every build, catching regressions and new disclosures early.
 Click to open the video
Click to open the video
Try VulnScout
You can get started with VulnScout in just a few minutes.
Check out the VulnScout GitHub repository for installation instructions, examples, and quick-start guides. If you use Yocto, check out meta-vulnscout, allowing for seamless integration with your image recipes.
Run it locally or in your CI pipeline to keep your open-source components under continuous watch and stay ahead of new vulnerabilities.